THIS POST IS A PLACEHOLDER AND NOT A PROPER POST
Microsoft recently rolled out some significant updates to the Cloud Adoption Framework (CAF) — and if you’re hosting workloads in Azure, it’s time to take notice.
As an Azure Practice Lead working with customers across industries, I’ve seen firsthand how CAF shapes cloud strategy, governance, and landing zone design. This latest refresh tightens the screws on security, simplifies decision-making, and brings clarity to some long-standing grey areas.
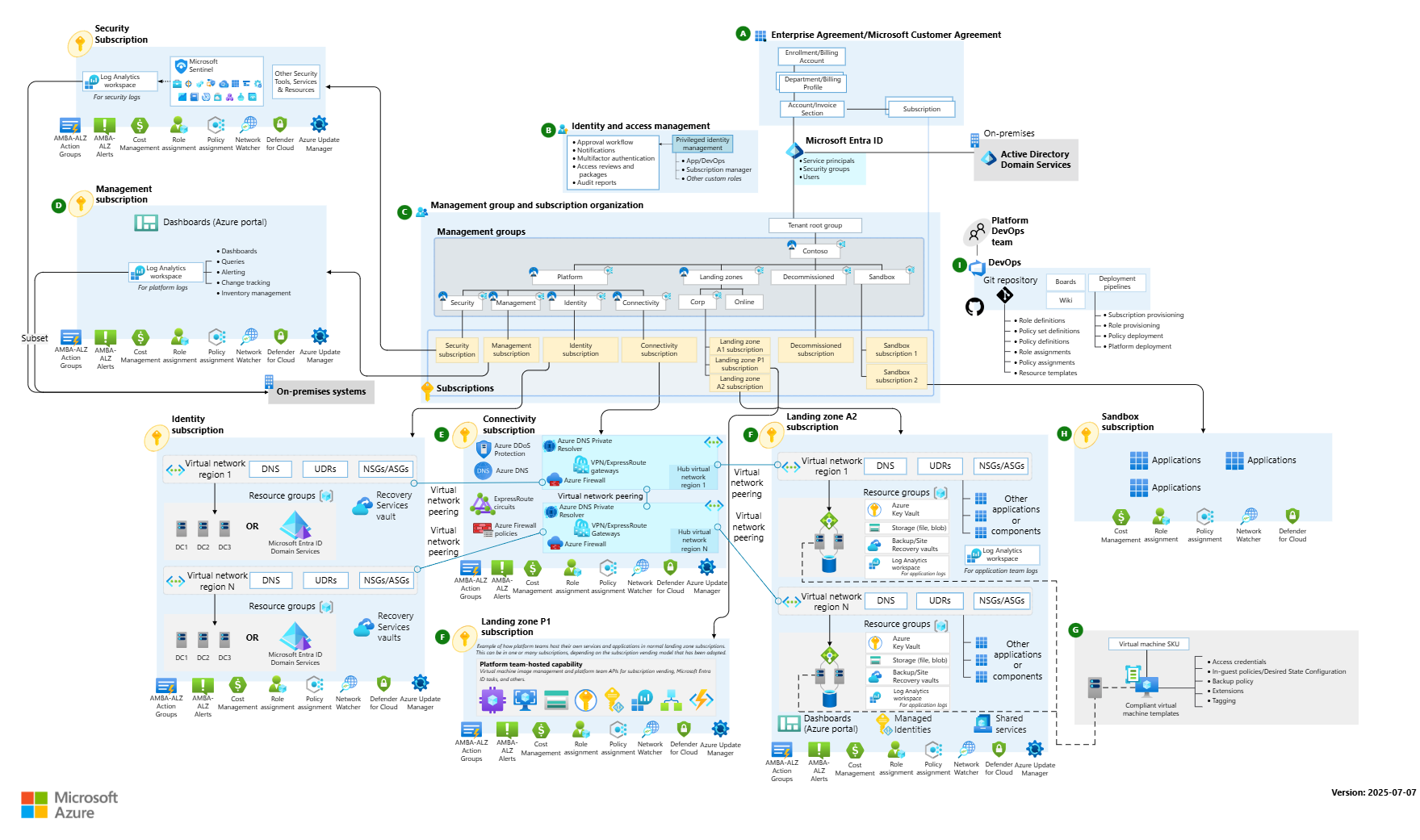
🔐 Security Landing Zone: Now a First-Class Citizen
The biggest headline? The Security Landing Zone is now officially part of the CAF lineup.
Previously, security guidance was scattered across governance and platform landing zone docs. Now, it’s consolidated into a dedicated Security Landing Zone blueprint, offering:
- Prescriptive controls aligned with Microsoft’s Cloud Security Benchmark
- Modular design for integrating with existing platform landing zones
- Built-in policy enforcement using Azure Policy and Defender for Cloud
- Guidance for Zero Trust architecture, identity segmentation, and workload isolation
This is a game-changer for customers in regulated industries or those scaling multi-tenant environments. It’s no longer a question of “how do I secure my landing zone?” — the blueprint gives you a clear path.
🧭 Governance Evolution: From Theory to Practice
CAF’s governance guidance has matured. The new updates emphasize:
- Policy-as-code: Governance is now treated as deployable infrastructure, not just documentation
- Role-based guardrails: Clear separation between platform, workload, and security teams
- Operational alignment: Integration with Azure Monitor, Log Analytics, and Defender for Cloud is now baked into governance recommendations
For customers, this means faster time-to-value and fewer surprises during audits or scale-out scenarios.
🧱 Workload Alignment: Landing Zones That Speak Your Language
The updated Landing Zone Conceptual Architecture now includes:
- Workload-centric variants: Whether you’re deploying SAP, AKS, or App Services, there’s tailored guidance
- Scalable design patterns: Support for hub-and-spoke, enterprise-scale, and subscription democratization
- Automation-first mindset: Bicep and Terraform modules are now front-and-center
This helps customers avoid over-engineering and focus on what matters: getting workloads production-ready with confidence.
🧠 What This Means for You
If you’re hosting workloads in Azure, here’s what you should do next:
- Review your current landing zone: Does it align with the new security blueprint?
- Revisit governance policies: Are they codified and enforced via Azure Policy?
- Map workloads to updated CAF guidance: Especially if you’re running regulated or mission-critical apps
And if you’re just starting your cloud journey — good news. The CAF is more actionable than ever.
📚 Resources to Dive Deeper
Here are some hand-picked links to help you explore the updates:
- CAF Security Landing Zone Overview
- CAF Governance Benchmark
- Landing Zone Conceptual Architecture
- Enterprise-Scale Bicep Modules
- Microsoft Cloud Security Benchmark
💬 Final Thoughts
CAF isn’t just a framework — it’s a living strategy. These updates reflect Microsoft’s commitment to making Azure adoption secure, scalable, and developer-friendly.
Whether you’re a cloud architect, security lead, or platform owner, now’s the time to align your approach with the new guidance.
If you’ve got questions or want to share how you’re implementing the new CAF updates, drop a comment or reach out. Let’s keep the conversation going.